
Difference: TWikiAccessControl (1 vs. 43)
Revision 432015-03-30 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
TWiki Access Control | ||||||||
| Line: 226 to 226 | ||||||||
| If it returns true, TWiki goes ahead and create the web without checking access control variables. Please read AllowWebCreateByUserMappingManager for more details. | ||||||||
| Added: | ||||||||
| > > | Forbid certain users to do certain actions by configurationYou may have an unruly registered users (e.g. a crawler program) who don't follow the rules while you don't have control over such users. And the web application container in which TWiki is installed may be managed by somebody else and you don't have tight and quick control. To cope with such situations, certain users can be forbidden certain scripts by setting{ForbidUserAction}.
A good example is worth more than a lengthy explanation, so here it is:
$TWiki::cfg{ForbidUserAction} = '
AggresiveCrawler: edit, oops, search;
ReadOnlyUser: !view, viewfile;
TotallyForbidden: !nothing;
';
In this example:
| |||||||
User masqueradingThere are cases where it's handy to access TWiki on behalf of somebody else retaining a trace of your real identity rather than completely becoming a different user. | ||||||||
| Line: 378 to 405 | ||||||||
You can have custom user/group notations such as USER:userid and LDAPGROUP:group-name and use them for access control. For example:
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| In a large organization, TWiki may need to depend on user and group data provided by its infrastructure. Custom user/group notations are handy in such situations though it's not trivial to implement. | ||||||||
Revision 422014-07-04 - TWikiContributor
| Line: 1 to 1 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
TWiki Access Control | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 16 to 16 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Your organization will learn that, while fostering an open collaborative environment, soft security (peer review), together with version control (complete audit trail) will take care of any security concern you might have. Open, free-form editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaborative environments. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with great care - the more restrictions, the less wiki in the mix. Experience shows that unrestricted write access works very well because: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| As a collaboration guideline: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Permissions settings of the webs on this TWiki site | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 233 to 237 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Dynamic access control | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | This feature is regarded experimental. There are pitfalls and vulnerability. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | There are pitfalls and you need to harden your web to avoid unexpected access. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Before using this feature, please read this entire section through carefully. You may want to restrict access dynamically -- based on topic name, a form field value, or some combination of factors. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 243 to 246 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Example 1 - restriction based on topic name | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Let's assume you need to restrict changes only to the CroniesGroup members excep with topics whose name ends with Public, which need be changed by anybody. That is achieve by the following settings on WebPrefences. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Let's assume you need to restrict changes only to the CroniesGroup members except with topics whose name ends with Public, which need be changed by anybody. That is achieve by the following settings on WebPrefences. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
* Set DYNAMIC_ACCESS_CONTROL = on | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 254 to 257 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Let's assume:
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | That is achieve by the following settings on WebPrefences. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | That is achieve by the following settings on WebPreferences. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
* Set DYNAMIC_ACCESS_CONTROL = on | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 319 to 322 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Vulnerability | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
Avoiding vulnerabilityBy default, user level preferences are read before web level preferences. This means a user can set a preferences variable at the user level and finalise it. To prevent this sort of attack, you need to harden your web or site by disabling user preferences by e.g. having the following line onlib/LocalSite.cfg
$TWiki::cfg{DemoteUserPreferences}= 1;
and having the following line on your WebPreferences and then finalise DENYUSERPREFEENCES.
* Set DENYUSERPREFEENCES = allPlease read TWikiVariables#ControllingUserLevelPrefsOverride for details. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | It's possible to redefine function tags such as %IF{...}% in your personal preferences. In a future release of TWiki, a way to prevent function tags from being overridden by personal preferences will be provied. But until then, you need to be well aware of this vulnerability. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Again by default, predefined variables such as %IF{...}% can be overridden by preferences variables.
If user preferences are disabled, ordinary users cannot attack using user preferences, but topic level preferences may cause unexpected consequences.
As such, all predefined variables need to be made un-overridable by having the following line on WebPreferences and then finalise OVERRIDABLEPREDEFINEDVARIABLES.
* Set OVERRIDABLEPREDEFINEDVARIABLES =Please read TWikiVariables#PredefinedVariables for details. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Disabling dynamic access control | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 439 to 459 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| It is possible to turn the PatternSkin and TopMenuSkin into read-only mode by removing the edit and attach controls (links and buttons). This is mainly useful if you have TWiki application pages or dashboards where you do not want regular users to change content. The read-only skin mode is not a replacement for access control; you can use it in addition to access control. Details at PatternSkinCustomization#ReadOnlySkinMode. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
Configuring access control for topics of a certain name in all websYou may need to restrict access to topics of a certain name in all webs. For example, there might be an add-on refering to a certain topic of all webs. And the add-on does things only administrators are supposed to do. In that case, change to the topic needs to be restricted only to administrators and must not be overridable. Let's say there is AutomationAddOn which refers to WebAutomation of all webs. And WebAutomation needs to be modifable only by administrators. That can be achieved by the following configuration.
$TWiki::cfg{Access}{Topic}{WebAutomation} = {
DENYCHANGE => 'Main.AllUsersGroup',
};
In addition to ALLOWCHANGE, you can sepcify DENYCHANGE, ALLOWVIEW, DENYVIEW, ALLOWRENAME, and DENYRENAME as follows.
$TWiki::cfg{Access}{Topic}{SpecialTopic} = {
DENYVIEW => 'JoeSchmoe',
ALLOWVIEW => 'FooGroup',
};
$TWiki::cfg{Access}{Topic}{TOPICNAME} has precedence over DENYTOPIC* and ALLOWTOPIC*.
For example, if the configuration for WebAutomation is there as above, there is no way to allow non-adminsitrators to change the WebAutomation topic of any web.
As a way to configure access control, this may look crude.
The reason why configured this way is that this can be part of plugin/add-on/contrib's configuration.
For example, Config.spec of AutomationAddOn would have the following lines, with which proper access control to WebAutomation topics is implemented without the administrator knowing it.
$TWiki::cfg{Access}{Topic}{WebAutomation} = {
DENYCHANGE => 'Main.AllUsersGroup',
};
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Related Topics: AdminDocumentationCategory, TWikiUserAuthentication, AllowWebCreateByUserMappingManager, UserMasquerading, CustomUserGroupNotations, TWiki:TWiki.TWikiAccessControlSupplement | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Revision 412013-10-09 - TWikiContributor
| Line: 1 to 1 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
TWiki Access Control | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Restricting read and write access to topics and webs, by Users and groups TWiki Access Control allows you restrict access to single topics and entire webs, by individual user and by user Groups. Access control, combined with TWikiUserAuthentication, lets you easily create and manage an extremely flexible, fine-grained privilege system. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 12 to 13 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
An Important Control Consideration | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Open, freeform editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaboration tools. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with great care - the more restrictions, the less Wiki in the mix. Experience shows that unrestricted write access works very well because: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Your organization will learn that, while fostering an open collaborative environment, soft security (peer review), together with version control (complete audit trail) will take care of any security concern you might have. Open, free-form editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaborative environments. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with great care - the more restrictions, the less wiki in the mix. Experience shows that unrestricted write access works very well because: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 23 to 26 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Permissions settings of the webs on this TWiki site | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Note: Above table comes from SitePermissions | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Note: Above table comes from SitePermissions | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Authentication vs. Access Control | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 128 to 132 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
For example, set this to restrict a topic to be viewable only by the MarketingExecGroup:
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Remember when opening up access to specific topics within a restricted web that other topics in the web - for example, the WebLeftBar - may also be accessed when viewing the topics. The message you get when you are denied access should tell you what topic you were not permitted to access. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | See "How TWiki evaluates ALLOW/DENY settings" below for more on how ALLOW and DENY interacts. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Be careful with empty values for any of these. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
Allowing public access to specific topics in a restricted web | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | You may want to completely open up access to a specific topic within a restricted web - allowing access by anybody. There is a special group for that - Main.AllUsersGroup. The following setting allows view access to the topic by anybody even if they are not authenticated.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | The same rules apply to ALLOWTOPICCHANGE/DENYTOPICCHANGE and APPLYTOPICRENAME/DENYTOPICRENAME. Setting ALLOWTOPICCHANGE or ALLOWTOPICRENAME to en empty value means the same as not defining it. Setting DENYTOPICCHANGE or DENYTOPICRENAME to an empty value means that anyone can edit or rename the topic. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Alternatively, you can grant access only to authenticated users by Main.AllAuthUsersGroup. If an unauthenticated user accesses a topic having the following setting, they are asked to authenticate themself.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Remember when opening up access to specific topics within a restricted web that other topics in the web - for example, the WebLeftBar - may also be accessed when viewing the topics. The message you get when you are denied access should tell you what topic you were not permitted to access. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | As mentioned in the following section, meaning of an empty value set to DENYTOPICVIEW, DENYTOPICCHANGE, and DENYTOPICRENAME has been changed in TWiki 6.0.
To keep those TWiki topics having empty DENYTOPICOPERAION accessible by everybody, those need to be replaced with
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | See "How TWiki evaluates ALLOW/DENY settings" below for more on how ALLOW and DENY interacts. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | For that, tools/eliminate_emptydenytopic is provided.
After upgrading from pre 6.0 to post 6.0, you need to run it.
Empty values in access control variablesSetting an empty value to an access control variable is the same as not setting at all:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 185 to 202 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 198 to 215 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Allowing web creation by user mapping managerThere are cases where DENYROOTCHANGE, ALLOWROOTCHANGE, DENYWEBCHANGE, and ALLOWWEBCHANGE, and DENYWEBCHANGE are not capable enough to implement web creation permission you want. To cope with such cases, when a new web is created, thecanCreateWeb($cUID, $web) method of the user mapping manager is called if the method exists.
If it returns true, TWiki goes ahead and create the web without checking access control variables.
Please read AllowWebCreateByUserMappingManager for more details.
User masqueradingThere are cases where it's handy to access TWiki on behalf of somebody else retaining a trace of your real identity rather than completely becoming a different user. We call it user masquerading. TWiki provides a framework to implement that. Please read UserMasquerading for more information. This is an advanced feature and not many TWiki sites are using, but there is a part in the following section mentioning it, it's mentioned here.Dynamic access controlThis feature is regarded experimental. There are pitfalls and vulnerability. Before using this feature, please read this entire section through carefully. You may want to restrict access dynamically -- based on topic name, a form field value, or some combination of factors. To cope with such situations, the dynamic access control mechanism is provided. If you setDYNAMIC_ACCESS_CONTROL 'on' at WebPreferences of the web, TWiki variables in access control variables mentioned above are expanded.
Example 1 - restriction based on topic nameLet's assume you need to restrict changes only to the CroniesGroup members excep with topics whose name ends with Public, which need be changed by anybody. That is achieve by the following settings on WebPrefences.
* Set DYNAMIC_ACCESS_CONTROL = on
* Set ALLOWWEBCHANGE = %IF{"'%CALCULATE{$SUBSTRING(%TOPIC%, -6, 6)}%' = 'Public'" then="%WIKINAME%" else="CroniesGroup"}%
Example 2 - restriction based on form fieldLet's assume:
* Set DYNAMIC_ACCESS_CONTROL = on
* Set ALLOWWEBVIEW = %IF{"'%CALCULATE{$SUBSTRING(%TOPIC%, 1, 6)}%' = 'ReqEnt' and '%FORMFIELD{Requestor}%' != '%WIKINAME%'" then="SupportGroup" else="%WIKINAME%"}%
Specifically the following access control variables are subject to TWiki variable expansion in their values.
Dynamic access control in accessing a different web's topicLet's assume WebA has the following lines on WebPreferences.* Set DYNAMIC_ACCESS_CONTROL = on * Set MEMBERS = JaneSmith, JoeSchmoe * Set ALLOWWEBVIEW = %MEMBERS%This is not a good way to use dynamic access control but it does restrict accessonly to those listed in MEMBERS. However, access control doesn't work as expected when WebA.TopicB is accessed from WebC.TopicD by %INCLUDE{WebA.TopicB}% or other variables.
This is because %MEMBERS% is defined in WebA and may have a different value in other webs.
You may think the following lines cheat the access control on WebA but actually not.
* Set MEMBERS = %WIKINAME%
%INCLUDE{WebA.TopicB}%
This is because when a topic (e.g. WebC.TopicD) is accessed from browser and the topic refers to another topic in a different web (e.g. WebA.TopicB) and the different web employs dynamic access control, access to another topic is defined being on the safer side.
Topic level dynamic access controlOn a topic, it's possible to use a variable defined on the topic for topic level access restriction. E.g.* Set MEMBERS = JaneSmith, JoeSchmoe * Set ALLOWTOPICVIEW = %MEMBERS%[This is not a good way to use dynamic access control Dynamic access control and user masqueradingYour user mapping handler may be providing the UserMasquerading feature. In that case, you expect dynamic access control to just work when user masquerading is in effect. Otherwise, you cannot test if your dynamic access control configuration is working as expected on your own. Dynamic access control does work as expected even if user masquerading is in effect. For that, the following things are happening under the hood. Let's think about Example 2 mentioned above. When you masquerading as SomebodyElse, you need to be able to see SomebodyElse's requests only. In the access control setting, a form field value is compared with %WIKINAME%. While user masquerading is in effect, your wiki name is YourNameOnBehalfOfSomebodyElse. It cannot match the form field value. To make dynamic access control work under these circumstances, variable expansion for dynamic access control is skewed as follows. Specifically, the following variables are expanded to the value of SomeboyElse's rather than YourNameOnBehalfOfSomebodyElse's.
VulnerabilityIt's possible to redefine function tags such as %IF{...}% in your personal preferences. In a future release of TWiki, a way to prevent function tags from being overridden by personal preferences will be provied. But until then, you need to be well aware of this vulnerability.Disabling dynamic access controlYou may not be comfortable with dynamic access control because it may slow things down. Or you may not want to be bothered by questions raised by users about it. If so, you can disable it by setting DYNAMIC_ACCESS_CONTROL 'off' and then finalizing at the local site level. (cf. TWikiVariables#Setting_Preferences_Variables) | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Access control and INCLUDEALLOWTOPICVIEW and ALLOWTOPICCHANGE only applies to the topic in which the settings are defined. If a topic A includes another topic B, topic A does not inherit the access rights of the included topic B. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 207 to 338 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Customizing "access denied" messageWhen access is denied, a page as follows is displayed: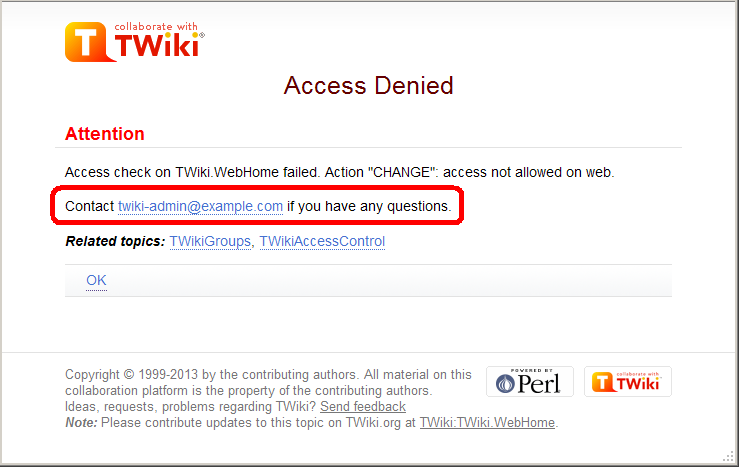 You may want to customize the passage annotated in the red rectangle.
For example, with a web restricting access, you may want to show the link to an access request form.
You can achieve that by setting
You may want to customize the passage annotated in the red rectangle.
For example, with a web restricting access, you may want to show the link to an access request form.
You can achieve that by setting TOPIC_ACCESS_CONTACT varialbe on WebPreferences. e.g.
* Set TOPIC_ACCESS_CONTACT = If you need to access this site, please apply [[Main.AccessForm][here]]Please note that setting it on a topic other than WebPreferences does not take effect. This is a limitation of the current implementation. Custom user/group notationsYou can have custom user/group notations such asUSER:userid and LDAPGROUP:group-name and use them for access control. For example:
* Set ALLOWWEBCHANGE = UID:buzz, LDAPGROUP:foo-barIn a large organization, TWiki may need to depend on user and group data provided by its infrastructure. Custom user/group notations are handy in such situations though it's not trivial to implement. Please read here for details. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Access Control quick recipes | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 284 to 441 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Related Topics: AdminDocumentationCategory, TWikiUserAuthentication, TWiki:TWiki.TWikiAccessControlSupplement | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Related Topics: AdminDocumentationCategory, TWikiUserAuthentication, AllowWebCreateByUserMappingManager, UserMasquerading, CustomUserGroupNotations, TWiki:TWiki.TWikiAccessControlSupplement | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
-- Contributors: TWiki:Main.PeterThoeny | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Revision 402012-09-11 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
TWiki Access ControlRestricting read and write access to topics and webs, by Users and groups | ||||||||
| Line: 150 to 150 | ||||||||
| By default, TWiki does not secure file attachments. Without making the following changes to the twiki.conf file, it is possible for anyone who has access to the server to gain access to an attachment if they know the attachment's fully qualified path, even though access to the topic associated with the attachment is secured. This is because attachments are referred to directly by Apache, and are not by default delivered via TWiki scripts. This means that the above instructions for controlling to topics do not apply to attachments unless you make the changes as described below. | ||||||||
| Changed: | ||||||||
| < < | An effective way to secure attachments is to apply the same access control settings to attachments as those applied to topics. This security enhancement can be accomplished by instructing the webserver via Apache's mod_rewrite module to redirect accesses to attachments via the TWiki viewfile script, which honors the TWiki access controls settings to topics. | |||||||
| > > | An effective way to secure attachments is to apply the same access control settings to attachments as those applied to topics. This security enhancement can be accomplished by instructing the webserver to redirect accesses to attachments via the TWiki viewfile script, which honors the TWiki access controls settings to topics. See the notes below for implications. | |||||||
The preferred method to secure attachments is by editing the twiki.conf file to include: | ||||||||
| Changed: | ||||||||
| < < | ScriptAlias /twiki/bin/ /filesystem/path/to/twiki/bin/ Alias /twiki/pub/ /filesystem/path/to/twiki/pub/ RewriteEngine on RewriteCond %{REQUEST_URI} !^/+twiki/+pub/+(TWiki|Sandbox)/+.+ RewriteRule ^/+twiki/+pub/+(.*)$ /twiki/bin/viewfile/$1 [L,PT] | |||||||
| > > | ScriptAlias /do /filesystem/path/to/twiki/bin Alias /pub/TWiki /filesystem/path/to/twiki/pub/TWiki Alias /pub/Sandbox /filesystem/path/to/twiki/pub/Sandbox ScriptAlias /pub /filesystem/path/to/twiki/bin/viewfile | |||||||
| Notes: | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Deleted: | ||||||||
| < < |
| |||||||
| ||||||||
| Line: 213 to 210 | ||||||||
Access Control quick recipes | ||||||||
| Added: | ||||||||
| > > | ||||||||
Restrict Access to Whole TWiki Site | ||||||||
| Changed: | ||||||||
| < < | For a firewalled TWiki, e.g. an intranet wiki or extranet wiki, you want to allow only invited people to access your TWiki. In this case, enable user authentication with ApacheLogin and lock down access to the whole twiki/bin and twiki/pub directories to all but valid users. In the Apache .htaccess file or the appropriate .conf file, replace the <FilesMatch "(attach|edit|... section with this: | |||||||
| > > | In a firewalled TWiki, e.g. an intranet wiki or extranet wiki, you want to allow only invited people to access your TWiki. There are three options:
1. Install TWiki Behind Firewall:
The firewall takes care of giving access to TWiki to authorized people only. This is a typical setup for a company wiki. As for TWiki configuration, no special setup is needed.
2. Extranet TWiki Using Template Login:
All TWiki content (pages and attachments) need to be access controlled. The Template Login allows users to login and logout. Only logged in users can access TWiki content.
Configuration: Follow the default setup, then change these configure settings:
twiki/bin and twiki/pub directories to all but valid users. In the Apache config file for TWiki (twiki.conf or .htaccess), replace the <FilesMatch "(attach|edit|... section with this: | |||||||
<FilesMatch ".*"> | ||||||||
| Line: 223 to 243 | ||||||||
| Changed: | ||||||||
| < < | If needed, you can further restrict access to selected webs with ALLOWWEBVIEW and other access control settings.
Note: With this configuration, someone with access to the site needs to register new users.
Authenticate all Webs and Restrict Selected Webs | |||||||
| > > | Notes: | |||||||
| Changed: | ||||||||
| < < | Use the following setup to authenticate users for topic viewing in all webs and to restrict access to selected webs. Requires TWikiUserAuthentication to be enabled.
| |||||||
| > > |
| |||||||
Authenticate and Restrict Selected Webs Only | ||||||||
Revision 392011-07-16 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
TWiki Access ControlRestricting read and write access to topics and webs, by Users and groups | ||||||||
| Line: 44 to 44 | ||||||||
A user can create an account in TWikiRegistration. The following actions are performed:
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 59 to 59 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | The ALLOWTOPICCHANGE setting defines who is allowed to change the group topic; it is a comma delimited list of users and groups. You typically want to restrict that to the members of the group itself, so it should contain the name of the topic. This prevents users not in the group from editing the topic to give themselves or others access. For example, for the KasabianGroup topic write:
| |||||||
| > > | The ALLOWTOPICCHANGE setting defines who is allowed to change the group topic; it is a comma delimited list of users and groups. You typically want to restrict that to the members of the group itself, so it should contain the name of the topic. This prevents users not in the group from editing the topic to give themselves or others access. For example, for the MarketingGroup topic write:
| |||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | ||||||||
The Super Admin Group | ||||||||
| Line: 72 to 72 | ||||||||
A number of TWiki functions (for example, renaming webs) are only available to administrators. Administrators are simply users who belong to the SuperAdminGroup. This is a standard user group, the name of which is defined by {SuperAdminGroup} setting in configure. The default name of this group is the TWikiAdminGroup. The system administrator may have chosen a different name for this group if your local TWiki uses an alternate group mapping manager but for simplicity we will use the default name TWikiAdminGroup in the rest of this topic.
You can create new administrators simply by adding them to the TWikiAdminGroup topic. For example, | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| A member of the Super Admin Group has unrestricted access throughout the TWiki, so only trusted staff should be added to this group. | ||||||||
| Line: 102 to 102 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | For example, set this to restrict a web to be viewable only by the MarketingGroup:
| |||||||
If your site allows hierarchical webs, then access to sub-webs is determined from the access controls of the parent web, plus the access controls in the sub-web. So, if the parent web has ALLOWWEBVIEW set, this will also apply to the subweb. Also note that you will need to ensure that the parent web's FINALPREFERENCES does not include the access control settings listed above. Otherwise you will not be able override the parent web's access control settings in sub-webs.
Creation and renaming of sub-webs is controlled by the WEBCHANGE setting on the parent web (or ROOTCHANGE for root webs). Renaming is additionally restricted by the setting of WEBRENAME in the web itself. | ||||||||
| Line: 122 to 125 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | For example, set this to restrict a topic to be viewable only by the MarketingExecGroup:
| |||||||
| Remember when opening up access to specific topics within a restricted web that other topics in the web - for example, the WebLeftBar - may also be accessed when viewing the topics. The message you get when you are denied access should tell you what topic you were not permitted to access. Be careful with empty values for any of these. | ||||||||
| Line: 168 to 174 | ||||||||
Controlling who can manage top-level websTop level webs are a special case, because they don't have a parent web with a WebPreferences. So there has to be a special control just for the root level. | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
ROOTCHANGE access to rename an existing top-level web. You just need WEBCHANGE in the web itself. | ||||||||
| Line: 207 to 213 | ||||||||
Access Control quick recipes | ||||||||
| Deleted: | ||||||||
| < < | Obfuscating WebsAnother way of hiding webs is to keep them hidden by not publishing the URL and by preventing theall webs search option from accessing obfuscated webs. Do so by enabling the NOSEARCHALL variable in WebPreferences:
| |||||||
Restrict Access to Whole TWiki SiteFor a firewalled TWiki, e.g. an intranet wiki or extranet wiki, you want to allow only invited people to access your TWiki. In this case, enable user authentication with ApacheLogin and lock down access to the wholetwiki/bin and twiki/pub directories to all but valid users. In the Apache .htaccess file or the appropriate .conf file, replace the <FilesMatch "(attach|edit|... section with this: | ||||||||
| Line: 262 to 259 | ||||||||
-->
| ||||||||
| Added: | ||||||||
| > > |
Obfuscating WebsAnother way of hiding webs is to keep them hidden by not publishing the URL and by preventing theall webs search option from accessing obfuscated webs. Do so by enabling the NOSEARCHALL variable in WebPreferences:
Read-only Skin ModeIt is possible to turn the PatternSkin and TopMenuSkin into read-only mode by removing the edit and attach controls (links and buttons). This is mainly useful if you have TWiki application pages or dashboards where you do not want regular users to change content. The read-only skin mode is not a replacement for access control; you can use it in addition to access control. Details at PatternSkinCustomization#ReadOnlySkinMode. | |||||||
|
Related Topics: AdminDocumentationCategory, TWikiUserAuthentication, TWiki:TWiki.TWikiAccessControlSupplement | ||||||||
Revision 382009-11-06 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
| Deleted: | ||||||||
| < < | ||||||||
TWiki Access ControlRestricting read and write access to topics and webs, by Users and groups | ||||||||
| Line: 140 to 139 | ||||||||
| See "How TWiki evaluates ALLOW/DENY settings" below for more on how ALLOW and DENY interacts. | ||||||||
| Changed: | ||||||||
| < < | Controlling access to Attachments | |||||||
| > > |
Securing File Attachments | |||||||
| Changed: | ||||||||
| < < | Attachments are referred to directly, and are not normally indirected via TWiki scripts. This means that the above instructions for access control will not apply to attachments. It is possible that someone may inadvertently publicise a URL that they expected to be access-controlled. | |||||||
| > > | By default, TWiki does not secure file attachments. Without making the following changes to the twiki.conf file, it is possible for anyone who has access to the server to gain access to an attachment if they know the attachment's fully qualified path, even though access to the topic associated with the attachment is secured. This is because attachments are referred to directly by Apache, and are not by default delivered via TWiki scripts. This means that the above instructions for controlling to topics do not apply to attachments unless you make the changes as described below. | |||||||
| Changed: | ||||||||
| < < | The easiest way to apply the same access control rules for attachments as apply to topics is to use the Apache mod_rewrite module, and configure your webserver to redirect accesses to attachments to the TWiki viewfile script. For example, | |||||||
| > > | An effective way to secure attachments is to apply the same access control settings to attachments as those applied to topics. This security enhancement can be accomplished by instructing the webserver via Apache's mod_rewrite module to redirect accesses to attachments via the TWiki viewfile script, which honors the TWiki access controls settings to topics.
The preferred method to secure attachments is by editing the twiki.conf file to include: | |||||||
ScriptAlias /twiki/bin/ /filesystem/path/to/twiki/bin/
Alias /twiki/pub/ /filesystem/path/to/twiki/pub/
RewriteEngine on | ||||||||
| Changed: | ||||||||
| < < | RewriteCond %{REQUEST_URI} !^/+twiki/+pub/+TWiki/+.+ RewriteRule ^/+twiki/+pub/+([^/]+)/+((([^/]+)/+)+)(.+) /twiki/bin/viewfile/$1/$4?filename=$5 [L,PT] | |||||||
| > > | RewriteCond %{REQUEST_URI} !^/+twiki/+pub/+(TWiki|Sandbox)/+.+ RewriteRule ^/+twiki/+pub/+(.*)$ /twiki/bin/viewfile/$1 [L,PT] | |||||||
| Changed: | ||||||||
| < < | That way all the controls that apply to the topic also apply to attachments to the topic. Other types of webserver have similar support.
Note: Images embedded in topics will load much slower since each image will be delivered by the viewfile script. | |||||||
| > > | Notes:
| |||||||
Controlling who can manage top-level webs | ||||||||
Revision 372009-03-03 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
TWiki Access Control | ||||||||
| Line: 34 to 34 | ||||||||
| Access control: Restrict access to content based on users and groups once a user is identified. | ||||||||
| Added: | ||||||||
| > > | ||||||||
Users and GroupsAccess control is based on the familiar concept of Users and Groups. Users are defined by their WikiNames. They can then be organized in unlimited combinations by inclusion in one or more user Groups. For convenience, Groups can also be included in other Groups. | ||||||||
| Added: | ||||||||
| > > | ||||||||
Managing UsersA user can create an account in TWikiRegistration. The following actions are performed: | ||||||||
| Line: 74 to 76 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | ||||||||
Restricting AccessYou can define who is allowed to read or write to a web or a topic. Note that some plugins may not respect access permissions. | ||||||||
| Line: 84 to 87 | ||||||||
| Note that there is an important distinction between CHANGE access and RENAME access. A user can CHANGE a topic, but thanks to version control their changes cannot be lost (the history of the topic before the change is recorded). However if a topic or web is renamed, that history may be lost. Typically a site will only give RENAME access to administrators and content owners. | ||||||||
| Added: | ||||||||
| > > | ||||||||
Controlling access to a WebYou can define restrictions on who is allowed to view a TWiki web. You can restrict access to certain webs to selected Users and Groups, by: | ||||||||
| Line: 108 to 112 | ||||||||
| Note: For Web level access rights Setting any of these settings to an empty value has the same effect as not setting them at all. Please note that the documentation of TWiki 4.0 and earlier versions of TWiki 4.1 did not reflect the actual implementation, e.g. an empty ALLOWWEBVIEW does not prevent anyone from viewing the web, and an an empty DENYWEBVIEW does not allow all to view the web. | ||||||||
| Added: | ||||||||
| > > | ||||||||
Controlling access to a Topic
| ||||||||
| Line: 134 to 139 | ||||||||
| See "How TWiki evaluates ALLOW/DENY settings" below for more on how ALLOW and DENY interacts. | ||||||||
| Added: | ||||||||
| > > | ||||||||
Controlling access to AttachmentsAttachments are referred to directly, and are not normally indirected via TWiki scripts. This means that the above instructions for access control will not apply to attachments. It is possible that someone may inadvertently publicise a URL that they expected to be access-controlled. | ||||||||
| Line: 162 to 168 | ||||||||
ROOTCHANGE access to rename an existing top-level web. You just need WEBCHANGE in the web itself. | ||||||||
| Added: | ||||||||
| > > | ||||||||
How TWiki evaluates ALLOW/DENY settingsWhen deciding whether to grant access, TWiki evaluates the following rules in order (read from the top of the list; if the logic arrives at PERMITTED or DENIED that applies immediately and no more rules are applied). You need to read the rules bearing in mind that VIEW, CHANGE and RENAME access may be granted/denied separately. | ||||||||
| Line: 192 to 199 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | ||||||||
Access Control quick recipesObfuscating Webs | ||||||||
Revision 362007-07-08 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
TWiki Access Control | ||||||||
| Line: 128 to 128 | ||||||||
| The same rules apply to ALLOWTOPICCHANGE/DENYTOPICCHANGE and APPLYTOPICRENAME/DENYTOPICRENAME. Setting ALLOWTOPICCHANGE or ALLOWTOPICRENAME to en empty value means the same as not defining it. Setting DENYTOPICCHANGE or DENYTOPICRENAME to an empty value means that anyone can edit or rename the topic. | ||||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | ||||||||
| See "How TWiki evaluates ALLOW/DENY settings" below for more on how ALLOW and DENY interacts. | ||||||||
| Line: 181 to 183 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | Access control and INCLUDEALLOWTOPICVIEW and ALLOWTOPICCHANGE only applies to the topic in which the settings are defined. If a topic A includes another topic B, topic A does not inherit the access rights of the included topic B. Examples: Topic A includes topic B
| |||||||
Access Control quick recipesObfuscating Webs | ||||||||
| Line: 228 to 239 | ||||||||
Hide Control Settings | ||||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | Edit topic preference settings under More topic actions menu. Preferences set in this manner are not visible in the topic text, but take effect nevertheless. Access control settings added as topic preference settings are stored in the topic meta data and they override settings defined in the topic text. | |||||||
| Alternatively, place them in HTML comment markers, but this exposes the access setting during ordinary editing. | ||||||||
Revision 352007-07-08 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
| Deleted: | ||||||||
| < < | On this page:
| |||||||
| Changed: | ||||||||
| < < |
TWiki Access Control | |||||||
| > > | TWiki Access Control | |||||||
| Restricting read and write access to topics and webs, by Users and groups | ||||||||
| Line: 10 to 8 | ||||||||
|
| ||||||||
| Added: | ||||||||
| > > | On this page:
| |||||||
An Important Control Consideration | ||||||||
| Line: 17 to 17 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 43 to 43 | ||||||||
A user can create an account in TWikiRegistration. The following actions are performed:
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | The default visitor name is TWikiGuest. This is the non-authenticated user. | |||||||
| > > | The default visitor name is TWikiGuest. This is the non-authenticated user. | |||||||
Managing GroupsThe following describes the standard TWiki support for groups. Your local TWiki may have an alternate group mapping manager installed. Check with your TWiki administrator if you are in doubt. | ||||||||
| Changed: | ||||||||
| < < | Groups are defined by group topics located in the Main web. To create a new group, visit TWikiGroups and enter the name of the new group ending in Group into the "new group" form field. This will create a new group topic with two important settings: | |||||||
| > > | Groups are defined by group topics located in the Main web. To create a new group, visit TWikiGroups and enter the name of the new group ending in Group into the "new group" form field. This will create a new group topic with two important settings: | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| The ALLOWTOPICCHANGE setting defines who is allowed to change the group topic; it is a comma delimited list of users and groups. You typically want to restrict that to the members of the group itself, so it should contain the name of the topic. This prevents users not in the group from editing the topic to give themselves or others access. For example, for the KasabianGroup topic write: | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
|
| ||||||||
| Line: 70 to 70 | ||||||||
A number of TWiki functions (for example, renaming webs) are only available to administrators. Administrators are simply users who belong to the SuperAdminGroup. This is a standard user group, the name of which is defined by {SuperAdminGroup} setting in configure. The default name of this group is the TWikiAdminGroup. The system administrator may have chosen a different name for this group if your local TWiki uses an alternate group mapping manager but for simplicity we will use the default name TWikiAdminGroup in the rest of this topic. | ||||||||
| Changed: | ||||||||
| < < | You can create new administrators simply by adding them to the TWikiAdminGroup topic. For example,
| |||||||
| > > | You can create new administrators simply by adding them to the TWikiAdminGroup topic. For example,
| |||||||
A member of the Super Admin Group has unrestricted access throughout the TWiki, so only trusted staff should be added to this group.
Restricting AccessYou can define who is allowed to read or write to a web or a topic. Note that some plugins may not respect access permissions. | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 99 to 99 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | If your site allows hierarchical webs, then access to sub-webs is determined from the access controls of the parent web, plus the access controls in the sub-web. So, if the parent web has ALLOWWEBVIEW set, this will also apply to the subweb. | |||||||
| > > | If your site allows hierarchical webs, then access to sub-webs is determined from the access controls of the parent web, plus the access controls in the sub-web. So, if the parent web has ALLOWWEBVIEW set, this will also apply to the subweb. Also note that you will need to ensure that the parent web's FINALPREFERENCES does not include the access control settings listed above. Otherwise you will not be able override the parent web's access control settings in sub-webs. | |||||||
| Creation and renaming of sub-webs is controlled by the WEBCHANGE setting on the parent web (or ROOTCHANGE for root webs). Renaming is additionally restricted by the setting of WEBRENAME in the web itself. | ||||||||
| Added: | ||||||||
| > > | Note: If you restrict access to the Main, make sure to add the TWikiRegistrationAgent so that users can register. Example:
| |||||||
Note: For Web level access rights Setting any of these settings to an empty value has the same effect as not setting them at all. Please note that the documentation of TWiki 4.0 and earlier versions of TWiki 4.1 did not reflect the actual implementation, e.g. an empty ALLOWWEBVIEW does not prevent anyone from viewing the web, and an an empty DENYWEBVIEW does not allow all to view the web.
Controlling access to a Topic | ||||||||
| Line: 152 to 155 | ||||||||
Controlling who can manage top-level websTop level webs are a special case, because they don't have a parent web with a WebPreferences. So there has to be a special control just for the root level. | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
ROOTCHANGE access to rename an existing top-level web. You just need WEBCHANGE in the web itself. | ||||||||
| Line: 189 to 192 | ||||||||
|
| ||||||||
| Added: | ||||||||
| > > | Restrict Access to Whole TWiki SiteFor a firewalled TWiki, e.g. an intranet wiki or extranet wiki, you want to allow only invited people to access your TWiki. In this case, enable user authentication with ApacheLogin and lock down access to the wholetwiki/bin and twiki/pub directories to all but valid users. In the Apache .htaccess file or the appropriate .conf file, replace the <FilesMatch "(attach|edit|... section with this:
<FilesMatch ".*">
require valid-user
</FilesMatch>
If needed, you can further restrict access to selected webs with ALLOWWEBVIEW and other access control settings.
Note: With this configuration, someone with access to the site needs to register new users. | |||||||
Authenticate all Webs and Restrict Selected WebsUse the following setup to authenticate users for topic viewing in all webs and to restrict access to selected webs. Requires TWikiUserAuthentication to be enabled. | ||||||||
| Added: | ||||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Authenticate and Restrict Selected Webs Only | ||||||||
| Line: 205 to 224 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Hide Control Settings | ||||||||
| Line: 215 to 234 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | * Set DENYTOPICCHANGE = Main.SomeGroup | |||||||
| > > | * Set DENYTOPICCHANGE = Main.SomeGroup | |||||||
-->
| ||||||||
Revision 342007-03-02 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 17 to 17 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 51 to 51 | ||||||||
Managing Groups | ||||||||
| Changed: | ||||||||
| < < | Groups are defined by group topics located in the Main web, such as the TWikiAdminGroup. To create a new group, visit TWikiGroups and enter the name of the new group ending in Group into the "new group" form field. This will create a new group topic with two important settings: | |||||||
| > > | The following describes the standard TWiki support for groups. Your local TWiki may have an alternate group mapping manager installed. Check with your TWiki administrator if you are in doubt.
Groups are defined by group topics located in the Main web. To create a new group, visit TWikiGroups and enter the name of the new group ending in Group into the "new group" form field. This will create a new group topic with two important settings: | |||||||
| ||||||||
| Changed: | ||||||||
| < < | The ALLOWTOPICCHANGE setting defines who is allowed to change the group topic; it is a comma delimited list of users and groups. You typically want to restrict that to the members of the group itself, so it should contain the name of the topic. This prevents users not in the group from editing the topic to give themselves or others access. For example, for the TWikiAdminGroup topic write:
| |||||||
| > > | The ALLOWTOPICCHANGE setting defines who is allowed to change the group topic; it is a comma delimited list of users and groups. You typically want to restrict that to the members of the group itself, so it should contain the name of the topic. This prevents users not in the group from editing the topic to give themselves or others access. For example, for the KasabianGroup topic write:
| |||||||
The Super Admin Group | ||||||||
| Changed: | ||||||||
| < < | By mistyping a user or group name in the settings, it's possible to lock a topic so that no-one can edit it from a browser. To avoid this, add the WikiNames of registered administrators to the super admin group topic called TWikiAdminGroup. The name of this topic is defined by the {SuperAdminGroup} configure setting. Example group setting: | |||||||
| > > | A number of TWiki functions (for example, renaming webs) are only available to administrators. Administrators are simply users who belong to the SuperAdminGroup. This is a standard user group, the name of which is defined by {SuperAdminGroup} setting in configure. The default name of this group is the TWikiAdminGroup. The system administrator may have chosen a different name for this group if your local TWiki uses an alternate group mapping manager but for simplicity we will use the default name TWikiAdminGroup in the rest of this topic.
You can create new administrators simply by adding them to the TWikiAdminGroup topic. For example, | |||||||
| ||||||||
| Added: | ||||||||
| > > | A member of the Super Admin Group has unrestricted access throughout the TWiki, so only trusted staff should be added to this group. | |||||||
Restricting Access | ||||||||
| Line: 75 to 80 | ||||||||
| ||||||||
| Added: | ||||||||
| > > |
| |||||||
Controlling access to a Web | ||||||||
| Line: 88 to 96 | ||||||||
| ||||||||
| Added: | ||||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | Be careful with empty values for any of these. In older versions of TWiki,
| |||||||
| > > | If your site allows hierarchical webs, then access to sub-webs is determined from the access controls of the parent web, plus the access controls in the sub-web. So, if the parent web has ALLOWWEBVIEW set, this will also apply to the subweb.
Creation and renaming of sub-webs is controlled by the WEBCHANGE setting on the parent web (or ROOTCHANGE for root webs). Renaming is additionally restricted by the setting of WEBRENAME in the web itself.
Note: For Web level access rights Setting any of these settings to an empty value has the same effect as not setting them at all. Please note that the documentation of TWiki 4.0 and earlier versions of TWiki 4.1 did not reflect the actual implementation, e.g. an empty ALLOWWEBVIEW does not prevent anyone from viewing the web, and an an empty DENYWEBVIEW does not allow all to view the web. | |||||||
Controlling access to a Topic | ||||||||
| Line: 102 to 112 | ||||||||
| ||||||||
| Added: | ||||||||
| > > |
| |||||||
| Remember when opening up access to specific topics within a restricted web that other topics in the web - for example, the WebLeftBar - may also be accessed when viewing the topics. The message you get when you are denied access should tell you what topic you were not permitted to access. | ||||||||
| Changed: | ||||||||
| < < | Be careful with empty values for any of these. In older versions of TWiki,
| |||||||
| > > | Be careful with empty values for any of these.
| |||||||
Controlling access to Attachments | ||||||||
| Line: 130 to 148 | ||||||||
Note: Images embedded in topics will load much slower since each image will be delivered by the viewfile script. | ||||||||
| Changed: | ||||||||
| < < | Controlling who can create top-level webs | |||||||
| > > |
Controlling who can manage top-level webs | |||||||
Top level webs are a special case, because they don't have a parent web with a WebPreferences. So there has to be a special control just for the root level.
| ||||||||
| Line: 139 to 159 | ||||||||
How TWiki evaluates ALLOW/DENY settings | ||||||||
| Changed: | ||||||||
| < < | When deciding whether to grant access, TWiki evaluates the following rules in order (read from the top of the list; if the logic arrives at PERMITTED or DENIED that applies immediately and no more rules are applied). You need to read the rules bearing in mind that VIEW and CHANGE access may be granted/denied separately.
| |||||||
| > > | When deciding whether to grant access, TWiki evaluates the following rules in order (read from the top of the list; if the logic arrives at PERMITTED or DENIED that applies immediately and no more rules are applied). You need to read the rules bearing in mind that VIEW, CHANGE and RENAME access may be granted/denied separately.
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Deleted: | ||||||||
| < < |
| |||||||
Access Control quick recipes | ||||||||
Revision 332006-10-13 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 66 to 66 | ||||||||
The Super Admin Group | ||||||||
| Changed: | ||||||||
| < < | By mistyping a user or group name in the settings, it's possible to lock a topic so that no-one can edit it from a browser. To avoid this, add the WikiNames of registered administrators to the super admin group topic called TWikiAdminGroup. The name of this topic is defined by the {SuperAdminGroup} configure setting. Example group setting: | |||||||
| > > | By mistyping a user or group name in the settings, it's possible to lock a topic so that no-one can edit it from a browser. To avoid this, add the WikiNames of registered administrators to the super admin group topic called TWikiAdminGroup. The name of this topic is defined by the {SuperAdminGroup} configure setting. Example group setting: | |||||||
Restricting Access | ||||||||
| Line: 75 to 75 | ||||||||
| ||||||||
| Deleted: | ||||||||
| < < |
| |||||||
Controlling access to a Web | ||||||||
| Changed: | ||||||||
| < < | You can define restrictions of who is allowed to view a TWiki web. You can restrict access to certain webs to selected Users and Groups, by: | |||||||
| > > | You can define restrictions on who is allowed to view a TWiki web. You can restrict access to certain webs to selected Users and Groups, by: | |||||||
| ||||||||
| Line: 91 to 88 | ||||||||
| ||||||||
| Deleted: | ||||||||
| < < |
| |||||||
Be careful with empty values for any of these. In older versions of TWiki,
| ||||||||
| Line: 102 to 97 | ||||||||
Controlling access to a Topic | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Deleted: | ||||||||
| < < |
| |||||||
| Remember when opening up access to specific topics within a restricted web that other topics in the web - for example, the WebLeftBar - may also be accessed when viewing the topics. The message you get when you are denied access should tell you what topic you were not permitted to access. | ||||||||
| Line: 131 to 124 | ||||||||
| RewriteEngine on RewriteCond %{REQUEST_URI} !^/+twiki/+pub/+TWiki/+.+ RewriteRule ^/+twiki/+pub/+([^/]+)/+((([^/]+)/+)+)(.+) /twiki/bin/viewfile/$1/$4?filename=$5 [L,PT] | ||||||||
| Changed: | ||||||||
| < < | </verbatim | |||||||
| > > | ||||||||
That way all the controls that apply to the topic also apply to attachments to the topic. Other types of webserver have similar support.
Note: Images embedded in topics will load much slower since each image will be delivered by the viewfile script. | ||||||||
| Added: | ||||||||
| > > | Controlling who can create top-level websTop level webs are a special case, because they don't have a parent web with a WebPreferences. So there has to be a special control just for the root level.
ROOTCHANGE access to rename an existing top-level web. You just need WEBCHANGE in the web itself. | |||||||
How TWiki evaluates ALLOW/DENY settings | ||||||||
| Changed: | ||||||||
| < < | When deciding whether to grant access, TWiki evaluates the following rules in order (read from the top of the list; if the logic arrives at PERMITTED or DENIED that applies immediately and no more rules are applied). You need to read the rules bearing in mind that VIEW, CHANGE and RENAME access may be granted/denied separately. | |||||||
| > > | When deciding whether to grant access, TWiki evaluates the following rules in order (read from the top of the list; if the logic arrives at PERMITTED or DENIED that applies immediately and no more rules are applied). You need to read the rules bearing in mind that VIEW and CHANGE access may be granted/denied separately. | |||||||
| ||||||||
| Line: 189 to 189 | ||||||||
Hide Control Settings | ||||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | ||||||||
| ||||||||
Revision 322005-11-11 - TWikiContributor
Revision 312005-11-11 - TWikiContributor
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 10 to 10 | ||||||||
|
| ||||||||
| Added: | ||||||||
| > > | ||||||||
An Important Control ConsiderationOpen, freeform editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaboration tools. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with great care - the more restrictions, the less Wiki in the mix. Experience shows that unrestricted write access works very well because: | ||||||||
| Line: 166 to 167 | ||||||||
| This setup can be useful to hide a new web until content its ready for deployment, or to hide view access restricted webs. | ||||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | ||||||||
Authenticate all Webs and Restrict Selected Webs | ||||||||
| Line: 176 to 177 | ||||||||
| ||||||||
| Deleted: | ||||||||
| < < |
| |||||||
Authenticate and Restrict Selected Webs Only | ||||||||
| Line: 187 to 186 | ||||||||
| ||||||||
| Deleted: | ||||||||
| < < |
| |||||||
Hide Control Settings | ||||||||
Revision 302005-11-11 - TWikiContributor
| Line: 1 to 1 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
On this page:
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 6 to 6 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Restricting read and write access to topics and webs, by Users and groups | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | TWikiAccessControl allows you restrict access to single topics and entire webs, by individual user and by user Groups, in three areas: view; edit & attach; and rename/move/delete. Access control, combined with TWikiUserAuthentication, lets you easily create and manage an extremely flexible, fine-grained privilege system. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | TWiki Access Control allows you restrict access to single topics and entire webs, by individual user and by user Groups. Access control, combined with TWikiUserAuthentication, lets you easily create and manage an extremely flexible, fine-grained privilege system. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | An Important Control Consideration | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Open, freeform editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaboration tools. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with care - the more restrictions, the less Wiki in the mix. Experience shows that unrestricted write access works very well because: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | An Important Control Consideration | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Open, freeform editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaboration tools. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with great care - the more restrictions, the less Wiki in the mix. Experience shows that unrestricted write access works very well because: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 19 to 18 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deleted: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| As a collaboration guideline: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deleted: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Permissions settings of the webs on this TWiki site
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Authentication vs. Access ControlAuthentication: Identifies who a user is based on a login procedure. See TWikiUserAuthentication. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 38 to 40 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Managing UsersA user can create an account in TWikiRegistration. The following actions are performed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deleted: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Users can be authenticated using Basic Authentication (htaccess) or SSL (secure server). In either case, TWikiUserAuthentication is required in order to track user identities, and use User and Group access control. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
The default visitor name is TWikiGuest. This is the non-authenticated user.
Managing Groups | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Groups are defined by group topics created in the Main web, like the TWikiAdminGroup. To create a new group:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Groups are defined by group topics located in the Main web, such as the TWikiAdminGroup. To create a new group, visit TWikiGroups and enter the name of the new group ending in Group into the "new group" form field. This will create a new group topic with two important settings: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deleted: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
Restricting Write AccessYou can define who is allowed to make changes to a web or a topic.Deny Editing by TopicDenying editing of a topic also restricts file attachment; both privileges are assigned together.
Deny Editing by Web | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Restricting web-level editing blocks creating new topics, changing topics or attaching files. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | The GROUP setting is a comma-separated list of users and/or other groups. Example:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | The ALLOWTOPICCHANGE setting defines who is allowed to change the group topic; it is a comma delimited list of users and groups. You typically want to restrict that to the members of the group itself, so it should contain the name of the topic. This prevents users not in the group from editing the topic to give themselves or others access. For example, for the TWikiAdminGroup topic write:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | The same rules apply as for restricting topics, with these additions:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Restricting Rename Access | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
The Super Admin Group | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | You can define who is allowed to rename, move or delete a topic, or rename a web. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | By mistyping a user or group name in the settings, it's possible to lock a topic so that no-one can edit it from a browser. To avoid this, add the WikiNames of registered administrators to the super admin group topic called TWikiAdminGroup. The name of this topic is defined by the {SuperAdminGroup} configure setting. Example group setting:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Deny Renaming by Topic | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Restricting Access | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | To allow a user to rename, move or delete a topic, they also need write (editing) permission. They also need write access to change references in referring topics. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | You can define who is allowed to read or write to a web or a topic. Note that some plugins may not respect access permissions. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Controlling access to a Web | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | You can define restrictions of who is allowed to view a TWiki web. You can restrict access to certain webs to selected Users and Groups, by: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Deny Renaming by Web | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
Controlling access to a Topic
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | You can define restrictions of who is allowed to rename a TWiki web. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Controlling access to Attachments | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Attachments are referred to directly, and are not normally indirected via TWiki scripts. This means that the above instructions for access control will not apply to attachments. It is possible that someone may inadvertently publicise a URL that they expected to be access-controlled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | The same rules apply as for topics, with these additions:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | The easiest way to apply the same access control rules for attachments as apply to topics is to use the Apache mod_rewrite module, and configure your webserver to redirect accesses to attachments to the TWiki viewfile script. For example, | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Restricting Read Access | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | ScriptAlias /twiki/bin/ /filesystem/path/to/twiki/bin/ Alias /twiki/pub/ /filesystem/path/to/twiki/pub/ | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | You can define who is allowed to see a web. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | RewriteEngine on RewriteRule ^/twiki/pub/TWiki/(.*)$ /twiki/pub/TWiki/$1 [L,PT] RewriteRule ^/twiki/pub/([^\/]+)/([^\/]+)/([^\/]+)$ /twiki/bin/viewfile/$1/$2?filename=$3 [L,PT] | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Deny Viewing by Topic | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | That way all the controls that apply to the topic also apply to attachments to the topic. Other types of webserver have similar support. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | DENYTOPICVIEW / ALLOWTOPICVIEW preferences variables, provided that the view script is authenticated. However this setup is not recommended since all content is searchable within a web - a search will turn up view restricted topics. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Note: Images embedded in topics will load much slower since each image will be delivered by the viewfile script. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Deny Viewing by Web | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | How TWiki evaluates ALLOW/DENY settings | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | You can define restrictions of who is allowed to view a TWiki web. You can restrict access to certain webs to selected Users and Groups, by: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | When deciding whether to grant access, TWiki evaluates the following rules in order (read from the top of the list; if the logic arrives at PERMITTED or DENIED that applies immediately and no more rules are applied). You need to read the rules bearing in mind that VIEW, CHANGE and RENAME access may be granted/denied separately.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Access Control quick recipes | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Obfuscate Webs | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Obfuscating Webs | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | The idea is to keep a web hidden by not publishing its URL and by preventing the all webs search option from accessing obfuscated webs. Do so by enabling the NOSEARCHALL variable in WebPreferences: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Another way of hiding webs is to keep them hidden by not publishing the URL and by preventing the all webs search option from accessing obfuscated webs. Do so by enabling the NOSEARCHALL variable in WebPreferences: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | This setup can be useful to hide a new web until content its ready for deployment. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | This setup can be useful to hide a new web until content its ready for deployment, or to hide view access restricted webs. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Authenticate all Webs and Restrict Selected Webs | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Authenticate all Webs and Restrict Selected Webs | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Use the following setup to authenticate users for topic viewing in all webs and to restrict access to selected webs: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Use the following setup to authenticate users for topic viewing in all webs and to restrict access to selected webs. Requires TWikiUserAuthentication to be enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 160 to 178 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deleted: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
view script is authenticated, which means that all Users have to login, even for read-only access. (An open guest account, like TWikiGuest, can get around this, allowing anyone to login to a common account with, for example, view-only access for public webs.) TWikiInstallationGuide has more on Basic Authentication, using the .htaccess file. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Authenticate and Restricting Selected Webs Only | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Authenticate and Restrict Selected Webs Only | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | Use the following setup to provide unrestricted viewing access to open webs, with authentication only on selected webs: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Use the following setup to provide unrestricted viewing access to open webs, with authentication only on selected webs. Requires TWikiUserAuthentication to be enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Line: 174 to 189 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deleted: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | When a user accesses a web where you enabled view restriction, TWiki will redirect from the view script to the viewauth script once (this happens only if the user has never edited a topic). Doing so will ask for authentication. The viewauth script shows the requested topic if the user could log on and if the user is authorized to see that web. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Hide Control Settings | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Changed: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
Hiding Control Settings<!-- * Set DENYTOPICCHANGE = Main.SomeGroup -->
The SuperAdminGroupBy mistyping a user or group name in the ALLOWTOPICCHANGE setting, it's possible to lock a topic so that no-one can edit it from a browser. To avoid this, you can create Web-based superusers:
$superAdminGroup = "TWikiAdminGroup"; | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deleted: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < < |
-- TWiki:Main.MikeMannix | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Added: | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| > > | Related Topics: AdminDocumentationCategory, TWikiUserAuthentication, TWiki:TWiki.TWikiAccessControlSupplement | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Revision 292004-08-15 - PeterThoeny
Revision 282003-04-14 - PeterThoeny
Revision 272002-12-29 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 31 to 31 | ||||||||
Managing Users | ||||||||
| Changed: | ||||||||
| < < | A user is created with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest. | |||||||
| > > | A user can create an account in TWikiRegistration. The following actions are performed: | |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Managing Groups | ||||||||
Revision 262002-05-29 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 144 to 144 | ||||||||
| ||||||||
| Added: | ||||||||
| > > |
| |||||||
| ||||||||
| Line: 157 to 158 | ||||||||
| ||||||||
| Added: | ||||||||
| > > |
| |||||||
| ||||||||
| Line: 170 to 172 | ||||||||
Hiding Control Settings | ||||||||
| Changed: | ||||||||
| < < |
<!-- | |||||||
| > > | <!-- * Set DENYTOPICCHANGE = Main.SomeGroup -->
| |||||||
The SuperAdminGroup | ||||||||
Revision 252002-05-29 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 112 to 112 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Restricting Web Access | |||||||
| > > | Restricting Read Access | |||||||
| Changed: | ||||||||
| < < | You can prevent selected Users and Groups from accessing certain webs, by hiding them using restricting read access, or by requiring login. There are two basic methods, one simple, using standard preferences variables to hide a web, but offering low security, and a secure log-in approach that is currently a workaround, involving some minor script and filesystem modification. | |||||||
| > > | You can define who is allowed to see a web. | |||||||
| Changed: | ||||||||
| < < | Create Hidden Webs | |||||||
| > > | Deny Viewing by Topic | |||||||
| Changed: | ||||||||
| < < | You can prevent selected Users and Groups from viewing certain TWiki webs by setting one or both of these variables in each web's WebPreferences topic: | |||||||
| > > | DENYTOPICVIEW / ALLOWTOPICVIEW preferences variables, provided that the view script is authenticated. However this setup is not recommended since all content is searchable within a web - a search will turn up view restricted topics.
Deny Viewing by WebYou can define restrictions of who is allowed to view a TWiki web. You can restrict access to certain webs to selected Users and Groups, by:
Obfuscate WebsThe idea is to keep a web hidden by not publishing its URL and by preventing theall webs search option from accessing obfuscated webs. Do so by enabling the NOSEARCHALL variable in WebPreferences:
Authenticate all Webs and Restrict Selected WebsUse the following setup to authenticate users for topic viewing in all webs and to restrict access to selected webs:
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
all webs search option from accessing hidden webs, by enabling the NOSEARCHALL variable in WebPreferences: | |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | view script is authenticated, which means that all Users have to login, even for read-only access. (An open guest account, like TWikiGuest, can get around this, allowing anyone to login to a common account with, for example, view-only access for public webs.) TWikiInstallationGuide has more on Basic Authentication, using the .htaccess file. | |||||||
| Changed: | ||||||||
| < < | Create Authenticated Access By Web | |||||||
| > > | Authenticate and Restricting Selected Webs Only | |||||||
| Use the following setup to provide unrestricted viewing access to open webs, with authentication only on selected webs: | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
view script to the viewauth script once (this happens only if the user has never edited a topic). Doing so will ask for authentication. The viewauth script shows the requested topic if the user could log on and if the user is authorized to see that web.
| |||||||
| Deleted: | ||||||||
| < < |
| |||||||
Hiding Control Settings | ||||||||
Revision 242002-05-12 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
TWiki Access Control | ||||||||
| Changed: | ||||||||
| < < | Restricting read and write access to topics and webs, by users and groups | |||||||
| > > | Restricting read and write access to topics and webs, by Users and groups | |||||||
| Changed: | ||||||||
| < < | TWikiAccessControl allows you restrict access to single topics and entire webs, by individual user and by user groups, in three main areas: view; edit & attach; and rename/move/delete. These controls, combined with TWikiUserAuthentication, let you easily create and manage an extremely flexible, fine-grained privilege system. | |||||||
| > > | TWikiAccessControl allows you restrict access to single topics and entire webs, by individual user and by user Groups, in three areas: view; edit & attach; and rename/move/delete. Access control, combined with TWikiUserAuthentication, lets you easily create and manage an extremely flexible, fine-grained privilege system. | |||||||
An Important Control Consideration | ||||||||
| Changed: | ||||||||
| < < | Open, freeform editing is the essence of the WikiCulture - it's what makes TWiki different and often more effective than other collaboration tools. So, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with care. Experience shows that unrestricted write access works very well because: | |||||||
| > > | Open, freeform editing is the essence of WikiCulture - what makes TWiki different and often more effective than other collaboration tools. For that reason, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with care - the more restrictions, the less Wiki in the mix. Experience shows that unrestricted write access works very well because: | |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < | As a collaboration guideline: | |||||||
| > > | As a collaboration guideline: | |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Users and Groups | ||||||||
| Changed: | ||||||||
| < < | Access control is based on users and groups. Users are defined by their WikiNames, an then organized in unlimited combinations under different user groups. | |||||||
| > > | Access control is based on the familiar concept of Users and Groups. Users are defined by their WikiNames. They can then be organized in unlimited combinations by inclusion in one or more user Groups. For convenience, Groups can also be included in other Groups. | |||||||
Managing Users | ||||||||
| Changed: | ||||||||
| < < | A user is created by with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest. | |||||||
| > > | A user is created with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest. | |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Managing Groups | ||||||||
| Changed: | ||||||||
| < < | Groups are defined by group topics in the Main web, like the TWikiAdminGroup. To create a new group:
| |||||||
| > > | Groups are defined by group topics created in the Main web, like the TWikiAdminGroup. To create a new group:
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Restricting Write Access | ||||||||
| Line: 59 to 57 | ||||||||
Denying editing of a topic also restricts file attachment; both privileges are assigned together.
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 75 to 73 | ||||||||
Restricting web-level editing blocks creating new topics, changing topics or attaching files.
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
The same rules apply as for restricting topics, with these additions:
| ||||||||
| Line: 91 to 89 | ||||||||
To allow a user to rename, move or delete a topic, they also need write (editing) permission. They also need write access to change references in referring topics.
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 107 to 105 | ||||||||
You can define restrictions of who is allowed to rename a TWiki web.
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
The same rules apply as for topics, with these additions:
| ||||||||
| Line: 116 to 114 | ||||||||
Restricting Web Access | ||||||||
| Changed: | ||||||||
| < < | You can prevent selected users and groups from accessing certain webs, by hiding them using restricting read access, or by requiring login. There are two basic methods, one simple, using standard preferences variables to hide a web, but offering low security, and a secure log-in approach that is currently a workaround, involving some minor script and filesystem modification. | |||||||
| > > | You can prevent selected Users and Groups from accessing certain webs, by hiding them using restricting read access, or by requiring login. There are two basic methods, one simple, using standard preferences variables to hide a web, but offering low security, and a secure log-in approach that is currently a workaround, involving some minor script and filesystem modification. | |||||||
Create Hidden Webs | ||||||||
| Changed: | ||||||||
| < < | You can prevent selected users and groups from viewing certain TWiki webs by setting one or both of these variables in each web's WebPreferences topic:
| |||||||
| > > | You can prevent selected Users and Groups from viewing certain TWiki webs by setting one or both of these variables in each web's WebPreferences topic:
| |||||||
all webs search option from accessing hidden webs, by enabling the NOSEARCHALL variable in WebPreferences:
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
|
| ||||||||
| Line: 142 to 140 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Hiding Control Settings
<!-- | ||||||||
| Changed: | ||||||||
| < < | Set DENYTOPICCHANGE = Main.SomeGroup | |||||||
| > > |
| |||||||
| --> | ||||||||
| Line: 157 to 155 | ||||||||
The SuperAdminGroupBy mistyping a user or group name in the ALLOWTOPICCHANGE setting, it's possible to lock a topic so that no-one can edit it from a browser. To avoid this, you can create Web-based superusers: | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
$superAdminGroup = "TWikiAdminGroup"; | ||||||||
| Line: 165 to 163 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | -- MikeMannix - 01 Apr 2002 -- PeterThoeny - 04 May 2002 | |||||||
| > > | -- PeterThoeny - 04 May 2002 -- MikeMannix - 12 May 2002 | |||||||
Revision 232002-05-04 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 17 to 17 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 38 to 38 | ||||||||
Managing Groups | ||||||||
| Changed: | ||||||||
| < < | Groups are defined by group topics in the Main web, like the TWikiAdminGroup. To start a new group:
| |||||||
| > > | Groups are defined by group topics in the Main web, like the TWikiAdminGroup. To create a new group:
| |||||||
Restricting Write Access | ||||||||
| Line: 59 to 59 | ||||||||
Denying editing of a topic also restricts file attachment; both privileges are assigned together.
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 73 to 75 | ||||||||
Restricting web-level editing blocks creating new topics, changing topics or attaching files.
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
The same rules apply as for restricting topics, with these additions:
| ||||||||
| Line: 89 to 91 | ||||||||
To allow a user to rename, move or delete a topic, they also need write (editing) permission. They also need write access to change references in referring topics.
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 103 to 107 | ||||||||
You can define restrictions of who is allowed to rename a TWiki web.
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
The same rules apply as for topics, with these additions:
| ||||||||
| Line: 117 to 121 | ||||||||
Create Hidden WebsYou can prevent selected users and groups from viewing certain TWiki webs by setting one or both of these variables in each web's WebPreferences topic: | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
all webs search option from accessing hidden webs, by enabling the NOSEARCHALL variable in WebPreferences: | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 129 to 133 | ||||||||
Create Authenticated Access By Web | ||||||||
| Changed: | ||||||||
| < < |
Example of viewing script
| |||||||
| > > | Use the following setup to provide unrestricted viewing access to open webs, with authentication only on selected webs: | |||||||
| ||||||||
| Line: 173 to 138 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | ||||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Hiding Control Settings | ||||||||
| Line: 199 to 165 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | -- MikeMannix - 01 Apr 2002 | |||||||
| > > | -- MikeMannix - 01 Apr 2002 -- PeterThoeny - 04 May 2002 | |||||||
Revision 222002-04-02 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 57 to 57 | ||||||||
Deny Editing by Topic | ||||||||
| Changed: | ||||||||
| < < | Denying editing of a topic also restricts attaching files to it; both privileges are assigned together. | |||||||
| > > | Denying editing of a topic also restricts file attachment; both privileges are assigned together. | |||||||
| ||||||||
| Line: 119 to 119 | ||||||||
You can prevent selected users and groups from viewing certain TWiki webs by setting one or both of these variables in each web's WebPreferences topic:
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
all webs search option from accessing hidden webs, by enabling the NOSEARCHALL variable in WebPreferences: | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Create Authenticated Access By Web | ||||||||
| Changed: | ||||||||
| < < | To selectively restrict web access with the security of Basic Authentication, there is a reliable workaround that involves some straightforward code modification: | |||||||
| > > | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | ||||||||
Example of viewing script redirect
#!/usr/bin/perl -w | ||||||||
| Line: 162 to 166 | ||||||||
| EOF | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | A SECOND OPTION: A less reliable workaround that also requires code changes is available to provide the same unrestricted viewing access, with authentication required only on selected webs: | |||||||
| > > | A SECOND OPTION: A less reliable workaround that doesn't involve code changes, but does require renaming a script, can provide the same generally unrestricted viewing access, with authentication only on selected webs: | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 184 to 190 | ||||||||
The SuperAdminGroup | ||||||||
| Changed: | ||||||||
| < < | By mistyping a user or group name in the ALLOWTOPICCHANGE setting, it's possible to lock a topic so that it no-one can edit it from a browser. To avoid this:
| |||||||
| > > | By mistyping a user or group name in the ALLOWTOPICCHANGE setting, it's possible to lock a topic so that no-one can edit it from a browser. To avoid this, you can create Web-based superusers:
| |||||||
$superAdminGroup = "TWikiAdminGroup"; | ||||||||
| Line: 193 to 199 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | -- MikeMannix - 20 Mar 2002 | |||||||
| > > | -- MikeMannix - 01 Apr 2002 | |||||||
Revision 212002-03-20 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 6 to 6 | ||||||||
| Restricting read and write access to topics and webs, by users and groups | ||||||||
| Deleted: | ||||||||
| < < | Overview | |||||||
TWikiAccessControl allows you restrict access to single topics and entire webs, by individual user and by user groups, in three main areas: view; edit & attach; and rename/move/delete. These controls, combined with TWikiUserAuthentication, let you easily create and manage an extremely flexible, fine-grained privilege system.
An Important Control Consideration | ||||||||
| Line: 29 to 27 | ||||||||
Users and Groups | ||||||||
| Changed: | ||||||||
| < < | Access control is based on users and groups. Users are defined by their WikiNames, an then organized into unlimited combinations under different user groups. | |||||||
| > > | Access control is based on users and groups. Users are defined by their WikiNames, an then organized in unlimited combinations under different user groups. | |||||||
Managing Users | ||||||||
| Line: 112 to 110 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Restricting Read Access | |||||||
| > > | Restricting Web Access | |||||||
| Changed: | ||||||||
| < < | You can define restrictions of who is allowed to view a TWiki web. | |||||||
| > > | You can prevent selected users and groups from accessing certain webs, by hiding them using restricting read access, or by requiring login. There are two basic methods, one simple, using standard preferences variables to hide a web, but offering low security, and a secure log-in approach that is currently a workaround, involving some minor script and filesystem modification. | |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > | Create Hidden WebsYou can prevent selected users and groups from viewing certain TWiki webs by setting one or both of these variables in each web's WebPreferences topic: | |||||||
| ||||||||
| Added: | ||||||||
| > > |
Create Authenticated Access By Web | |||||||
| Changed: | ||||||||
| < < | Known Issues | |||||||
| > > | To selectively restrict web access with the security of Basic Authentication, there is a reliable workaround that involves some straightforward code modification:
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > | Example of viewing script | |||||||
| Changed: | ||||||||
| < < | Selective Unrestricted Web Access | |||||||
| > > | chdir '..';
# Adjust SCRIPT and PATH_INFO variables to account for the changed directory
my $web = $ENV{SCRIPT_NAME};
$web =~ s#^.*/view(/[^/]*).*$#$1#; # isolate the path element after "view"
$ENV{PATH_TRANSLATED} =~ s#(/[^/]*)$#$web$1#;
$ENV{PATH_INFO} =~ s#(/[^/]*)$#$web$1#;
$ENV{SCRIPT_NAME} =~ s#/view$web#/view#;
$ENV{SCRIPT_FILENAME} =~ s#/view$web#/view#;
# open (LOG, '>>/tmp/redirect.log');
# print LOG join ("\n", scalar localtime (time ()), %ENV);
# close LOG;
exec ('/usr/bin/perl', '-wT', 'view.orig') or
print <<EOF;
Content-type: text/plain
Error executing /cgi-bin/view.orig: $?
Click the BACK button in your browser and contact webmaster\@bcs-oops.org.
EOF
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > | A SECOND OPTION: A less reliable workaround that also requires code changes is available to provide the same unrestricted viewing access, with authentication required only on selected webs: | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 158 to 193 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | -- MikeMannix - 02 Dec 2001 | |||||||
| > > | -- MikeMannix - 20 Mar 2002 | |||||||
Revision 202001-12-02 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 41 to 41 | ||||||||
Managing GroupsGroups are defined by group topics in theMain web, like the TWikiAdminGroup. To start a new group: | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Restricting Write Access | ||||||||
| Line: 135 to 137 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | Hiding Control Settings
<!-- | |||||||
The SuperAdminGroup | ||||||||
| Line: 147 to 158 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | -- PeterThoeny - 16 Mar 2001 -- AndreaSterbini - 11 Apr 2001 | |||||||
| > > | -- MikeMannix - 02 Dec 2001 | |||||||
Revision 192001-09-16 - MikeMannix
Revision 182001-09-14 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
|
Warning: Can't find topic TWiki.UtilTempDocNote
On this page:
| ||||||||
| Line: 10 to 10 | ||||||||
Overview | ||||||||
| Changed: | ||||||||
| < < | TWikiAccessControl allows you restrict access to single topics and entire webs, by individual user and by user groups, in three main areas: view; edit & attach; and rename/move/delete. These controls, combined with TWikiUserAuthentication, let you easily create and manage an extremely flexible, fine-grained privilege system. | |||||||
| > > | TWikiAccessControl allows you restrict access to single topics and entire webs, by individual user and by user groups, in three main areas: view; edit & attach; and rename/move/delete. These controls, combined with TWikiUserAuthentication, let you easily create and manage an extremely flexible, fine-grained privilege system. | |||||||
An Important Control Consideration | ||||||||
| Changed: | ||||||||
| < < | Open, freeform editing is the essence of the WikiCulture - it's what makes TWiki different and often more effective than other collaboration tools. So, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with care. Experience shows that unrestricted write access works very well because: | |||||||
| > > | Open, freeform editing is the essence of the WikiCulture - it's what makes TWiki different and often more effective than other collaboration tools. So, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with care. Experience shows that unrestricted write access works very well because: | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 35 to 35 | ||||||||
Managing Users | ||||||||
| Changed: | ||||||||
| < < | A user is created by with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest. | |||||||
| > > | A user is created by with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest. | |||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Managing Groups | ||||||||
| Line: 123 to 123 | ||||||||
Known Issues
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Selective Unrestricted Web Access
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
Revision 172001-09-12 - MikeMannix
Revision 162001-09-07 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Changed: | ||||||||
| < < | TWiki Access Control | |||||||
| > > | TWiki Access Control | |||||||
| Restricting read and write access to topics and webs, by users and groups | ||||||||
| Changed: | ||||||||
| < < | Overview | |||||||
| > > | Overview | |||||||
| TWikiAccessControl allows you restrict access to single topics and entire webs, by individual user and by user groups, in three main areas: view; edit & attach; and rename/move/delete. These controls, combined with TWikiUserAuthentication, let you easily create and manage an extremely flexible, fine-grained privilege system. | ||||||||
| Changed: | ||||||||
| < < | An Important Control Consideration | |||||||
| > > | An Important Control Consideration | |||||||
| Open, freeform editing is the essence of the WikiCulture - it's what makes TWiki different and often more effective than other collaboration tools. So, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with care. Experience shows that unrestricted write access works very well because: | ||||||||
| Line: 27 to 27 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Users and Groups | |||||||
| > > | Users and Groups | |||||||
| Access control is based on users and groups. Users are defined by their WikiNames, an then organized into unlimited combinations under different user groups. | ||||||||
| Changed: | ||||||||
| < < | Managing Users | |||||||
| > > | Managing Users | |||||||
A user is created by with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest.
| ||||||||
| Changed: | ||||||||
| < < | Managing Groups | |||||||
| > > | Managing Groups | |||||||
Groups are defined by group topics in the Main web, like the TWikiAdminGroup. To start a new group:
| ||||||||
| Line: 51 to 51 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Restricting Write Access | |||||||
| > > | Restricting Write Access | |||||||
| You can define who is allowed to make changes to a web or a topic. | ||||||||
| Changed: | ||||||||
| < < | Deny Editing by Topic | |||||||
| > > | Deny Editing by Topic | |||||||
Denying editing of a topic also restricts attaching files to it; both privileges are assigned together.
| ||||||||
| Line: 68 to 68 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Deny Editing by Web | |||||||
| > > | Deny Editing by Web | |||||||
| Restricting web-level editing blocks creating new topics, changing topics or attaching files. | ||||||||
| Line: 80 to 80 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Restricting Rename Access | |||||||
| > > | Restricting Rename Access | |||||||
| You can define who is allowed to rename, move or delete a topic, or rename a web. | ||||||||
| Changed: | ||||||||
| < < | Deny Renaming by Topic | |||||||
| > > | Deny Renaming by Topic | |||||||
| To allow a user to rename, move or delete a topic, they also need write (editing) permission. They also need write access to change references in referring topics. | ||||||||
| Line: 98 to 98 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Deny Renaming by Web | |||||||
| > > | Deny Renaming by Web | |||||||
| You can define restrictions of who is allowed to rename a TWiki web. | ||||||||
| Line: 110 to 110 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Restricting Read Access | |||||||
| > > | Restricting Read Access | |||||||
| You can define restrictions of who is allowed to view a TWiki web. | ||||||||
| Line: 118 to 118 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Known Issues | |||||||
| > > | Known Issues | |||||||
| ||||||||
| Changed: | ||||||||
| < < | Selective Unrestricted Web Access | |||||||
| > > | Selective Unrestricted Web Access | |||||||
| ||||||||
| Line: 136 to 136 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | The SuperAdminGroup | |||||||
| > > | The SuperAdminGroup | |||||||
By mistyping a user or group name in the ALLOWTOPICCHANGE setting, it's possible to lock a topic so that it no-one can edit it from a browser. To avoid this:
| ||||||||
Revision 152001-09-07 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 8 to 8 | ||||||||
Overview | ||||||||
| Changed: | ||||||||
| < < | TWiki allows you to define restrictions of who is allowed to view a TWiki web, make changes to topics or attach files. | |||||||
| > > | TWikiAccessControl allows you restrict access to single topics and entire webs, by individual user and by user groups, in three main areas: view; edit & attach; and rename/move/delete. These controls, combined with TWikiUserAuthentication, let you easily create and manage an extremely flexible, fine-grained privilege system.
An Important Control ConsiderationOpen, freeform editing is the essence of the WikiCulture - it's what makes TWiki different and often more effective than other collaboration tools. So, it is strongly recommended that decisions to restrict read or write access to a web or a topic are made with care. Experience shows that unrestricted write access works very well because: | |||||||
| Deleted: | ||||||||
| < < | IMPORTANT NOTE: Think twice before restricting read or write access to a web or a topic, because an open system where everybody can contribute is the essence of the WikiCulture. Experience shows that unrestricted write access works very well because: | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Users and Groups | ||||||||
| Changed: | ||||||||
| < < | Access control is based on users and groups. | |||||||
| > > | Access control is based on users and groups. Users are defined by their WikiNames, an then organized into unlimited combinations under different user groups. | |||||||
Managing Users | ||||||||
| Changed: | ||||||||
| < < | A user is created by with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest.
| |||||||
| > > | A user is created by with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest.
| |||||||
Managing Groups | ||||||||
| Changed: | ||||||||
| < < | Groups are defined by group topics in the Main web, like the TWikiAdminGroup.
| |||||||
| > > | Groups are defined by group topics in the Main web, like the TWikiAdminGroup. To start a new group:
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Restricting Write Access | ||||||||
| Changed: | ||||||||
| < < | Deny Editing by Topic | |||||||
| > > | You can define who is allowed to make changes to a web or a topic. | |||||||
| Changed: | ||||||||
| < < | You can define restrictions of who is allowed to make changes to a topic or attach files to it. | |||||||
| > > | Deny Editing by Topic | |||||||
| Changed: | ||||||||
| < < | Define one or both of these variables in a topic, preferably at the end of the topic: | |||||||
| > > | Denying editing of a topic also restricts attaching files to it; both privileges are assigned together.
| |||||||
| ||||||||
| Changed: | ||||||||
| < < | DENYTOPICCHANGE defines users or groups that are not allowed to make changes to the topic. It is a comma delimited list of users and groups. Example: * Set DENYTOPICCHANGE = Main.SomeBadBoy, Main.SomeBadGirl, Main.SomeHackerGroup | |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | ALLOWTOPICCHANGE defines users or groups that are allowed to make changes to the topic. It is a comma delimited list of users and groups. Example: * Set ALLOWTOPICCHANGE = Main.SomeGoodGuy, Main.SomeGoodGirl, Main.TWikiAdminGroup | |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | DENYTOPICCHANGE is evaluated before ALLOWTOPICCHANGE. Access is denied if the authenticated person is in the DENYTOPICCHANGE list, or not in the ALLOWTOPICCHANGE list. Access is granted in case DENYTOPICCHANGE and ALLOWTOPICCHANGE is not defined. | |||||||
| > > |
| |||||||
Deny Editing by Web | ||||||||
| Changed: | ||||||||
| < < | You can define restrictions of who is allowed to make changes to a TWiki web. This includes creating new topics, changing topics or attaching files. | |||||||
| > > | Restricting web-level editing blocks creating new topics, changing topics or attaching files. | |||||||
| Changed: | ||||||||
| < < | Define one or both of these variable in the WebPreferences topic: | |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < | The same rules apply like the one for Access Control for Individual Topics; with these additions: | |||||||
| > > | The same rules apply as for restricting topics, with these additions: | |||||||
Restricting Rename Access | ||||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | You can define who is allowed to rename, move or delete a topic, or rename a web. | |||||||
Deny Renaming by Topic | ||||||||
| Changed: | ||||||||
| < < | You can define restrictions of who is allowed to rename a topic. Note that users need this permission in addition to the CHANGE permission in order to rename a topic. They also need CHANGE access to change references in referring topics. | |||||||
| > > | To allow a user to rename, move or delete a topic, they also need write (editing) permission. They also need write access to change references in referring topics. | |||||||
| Changed: | ||||||||
| < < | Define one or both of these variables in a topic, preferably at the end of the topic: | |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < | DENYTOPICCRENAME defines users or groups that are not allowed to rename the topic. It is a comma delimited list of users and groups. Example: * Set DENYTOPICRENAME = Main.SomeBadBoy, Main.SomeBadGirl, Main.SomeHackerGroup | |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | ALLOWTOPICRENAME defines users or groups that are allowed to rename the topic. It is a comma delimited list of users and groups. Example: * Set ALLOWTOPICRENAME = Main.SomeGoodGuy, Main.SomeGoodGirl, Main.TWikiAdminGroup | |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | DENYTOPICRENAME is evaluated before ALLOWTOPICRENAME. Access is denied if the authenticated person is in the DENYTOPICRENAME list, or not in the ALLOWTOPICRENAME list. Access is granted in case DENYTOPICRENAME and ALLOWTOPICRENAME is not defined. | |||||||
| > > |
| |||||||
Deny Renaming by Web | ||||||||
| Changed: | ||||||||
| < < | You can define restrictions of who is allowed to do renames for a TWiki web. | |||||||
| > > | You can define restrictions of who is allowed to rename a TWiki web. | |||||||
| Changed: | ||||||||
| < < | Define one or both of these variable in the WebPreferences topic: | |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < | The same rules apply like the one for Access Control for Individual Topics; with these additions: | |||||||
| > > | The same rules apply as for topics, with these additions: | |||||||
| ||||||||
| Line: 101 to 114 | ||||||||
| You can define restrictions of who is allowed to view a TWiki web. | ||||||||
| Changed: | ||||||||
| < < | Define one or both of these variable in the WebPreferences topic: | |||||||
| > > |
| |||||||
| ||||||||
| Line: 113 to 126 | ||||||||
Selective Unrestricted Web Access
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Line: 125 to 138 | ||||||||
The SuperAdminGroup | ||||||||
| Changed: | ||||||||
| < < | The above schema can lock completely a topic in case of a typing error of the ALLOWTOPICCHANGE setting (see UnchangeableTopicBug
| |||||||
| > > | By mistyping a user or group name in the ALLOWTOPICCHANGE setting, it's possible to lock a topic so that it no-one can edit it from a browser. To avoid this:
| |||||||
$superAdminGroup = "TWikiAdminGroup"; | ||||||||
| Added: | ||||||||
| > > | ||||||||
| ||||||||
Revision 142001-09-05 - MikeMannix
Revision 132001-09-04 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
TWiki Access Control | ||||||||
| Added: | ||||||||
| > > | Restricting read and write access to topics and webs, by users and groups
Overview | |||||||
| TWiki allows you to define restrictions of who is allowed to view a TWiki web, make changes to topics or attach files. IMPORTANT NOTE: Think twice before restricting read or write access to a web or a topic, because an open system where everybody can contribute is the essence of the WikiCulture. Experience shows that unrestricted write access works very well because: | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
Users and GroupsAccess control is based on users and groups. | ||||||||
| Changed: | ||||||||
| < < | Users are defined by the user topics in the Main web, i.e. TWikiGuest
| |||||||
| > > | Managing UsersA user is created by with the TWikiRegistration form. The process generates a topic in the Main web in the new user's WikiName. The default visitor name is TWikiGuest.
Managing Groups | |||||||
| Changed: | ||||||||
| < < | Groups are defined by group topics in the Main web, i.e. TWikiAdminGroup
| |||||||
| > > | Groups are defined by group topics in the Main web, like the TWikiAdminGroup.
| |||||||
| ||||||||
| Added: | ||||||||
| > > | ||||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Added: | ||||||||
| > > | Restricting Write Access | |||||||
| Changed: | ||||||||
| < < | Write Access Restriction by Topic | |||||||
| > > | Deny Editing by Topic | |||||||
| You can define restrictions of who is allowed to make changes to a topic or attach files to it. | ||||||||
| Line: 42 to 55 | ||||||||
| DENYTOPICCHANGE is evaluated before ALLOWTOPICCHANGE. Access is denied if the authenticated person is in the DENYTOPICCHANGE list, or not in the ALLOWTOPICCHANGE list. Access is granted in case DENYTOPICCHANGE and ALLOWTOPICCHANGE is not defined. | ||||||||
| Changed: | ||||||||
| < < | Write Access Restriction by Web | |||||||
| > > | Deny Editing by Web | |||||||
| You can define restrictions of who is allowed to make changes to a TWiki web. This includes creating new topics, changing topics or attaching files. | ||||||||
| Line: 54 to 67 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Rename Access Restriction by Topic | |||||||
| > > | Restricting Rename AccessDeny Renaming by Topic | |||||||
| You can define restrictions of who is allowed to rename a topic. Note that users need this permission in addition to the CHANGE permission in order to rename a topic. They also need CHANGE access to change references in referring topics. | ||||||||
| Line: 68 to 85 | ||||||||
| DENYTOPICRENAME is evaluated before ALLOWTOPICRENAME. Access is denied if the authenticated person is in the DENYTOPICRENAME list, or not in the ALLOWTOPICRENAME list. Access is granted in case DENYTOPICRENAME and ALLOWTOPICRENAME is not defined. | ||||||||
| Changed: | ||||||||
| < < | Rename Access Restriction by Web | |||||||
| > > | Deny Renaming by Web | |||||||
| You can define restrictions of who is allowed to do renames for a TWiki web. | ||||||||
| Line: 80 to 97 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Read Access Restriction by Web | |||||||
| > > | Restricting Read Access | |||||||
| You can define restrictions of who is allowed to view a TWiki web. | ||||||||
| Line: 88 to 105 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Read Restriction Known Issues | |||||||
| > > | Known Issues | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
Selective Unrestricted Web Access | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
The SuperAdminGroup | ||||||||
| Changed: | ||||||||
| < < | The above schema can lock completely a topic in case of a typing error of the ALLOWTOPICCHANGE setting (see UnchangeableTopicBug
| |||||||
| > > | The above schema can lock completely a topic in case of a typing error of the ALLOWTOPICCHANGE setting (see UnchangeableTopicBug
| |||||||
| $superAdminGroup = "TWikiAdminGroup"; | ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
|
-- PeterThoeny - 16 Mar 2001 -- AndreaSterbini - 11 Apr 2001 | ||||||||
Revision 122001-08-31 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
On this page:
| ||||||||
| Line: 88 to 88 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Read Access Restriction Notes | |||||||
| > > | Read Restriction Known Issues | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
| Deleted: | ||||||||
| < < |
| |||||||
| Changed: | ||||||||
| < < | The SuperAdminGroup | |||||||
| > > | The SuperAdminGroup | |||||||
The above schema can lock completely a topic in case of a typing error of the ALLOWTOPICCHANGE setting (see UnchangeableTopicBug
| ||||||||
Revision 112001-08-30 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
| Added: | ||||||||
| > > | On this page:
| |||||||
TWiki Access ControlTWiki allows you to define restrictions of who is allowed to view a TWiki web, make changes to topics or attach files. | ||||||||
| Line: 25 to 28 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Write Access Restriction for Individual Topics | |||||||
| > > | Write Access Restriction by Topic | |||||||
| You can define restrictions of who is allowed to make changes to a topic or attach files to it. | ||||||||
| Line: 39 to 42 | ||||||||
| DENYTOPICCHANGE is evaluated before ALLOWTOPICCHANGE. Access is denied if the authenticated person is in the DENYTOPICCHANGE list, or not in the ALLOWTOPICCHANGE list. Access is granted in case DENYTOPICCHANGE and ALLOWTOPICCHANGE is not defined. | ||||||||
| Changed: | ||||||||
| < < | Write Access Restriction for a Whole TWiki Web | |||||||
| > > | Write Access Restriction by Web | |||||||
| You can define restrictions of who is allowed to make changes to a TWiki web. This includes creating new topics, changing topics or attaching files. | ||||||||
| Line: 51 to 54 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Rename Access Restriction for Individual Topics | |||||||
| > > | Rename Access Restriction by Topic | |||||||
| You can define restrictions of who is allowed to rename a topic. Note that users need this permission in addition to the CHANGE permission in order to rename a topic. They also need CHANGE access to change references in referring topics. | ||||||||
| Line: 65 to 68 | ||||||||
| DENYTOPICRENAME is evaluated before ALLOWTOPICRENAME. Access is denied if the authenticated person is in the DENYTOPICRENAME list, or not in the ALLOWTOPICRENAME list. Access is granted in case DENYTOPICRENAME and ALLOWTOPICRENAME is not defined. | ||||||||
| Changed: | ||||||||
| < < | Rename Access Restriction for a Whole TWiki Web | |||||||
| > > | Rename Access Restriction by Web | |||||||
| You can define restrictions of who is allowed to do renames for a TWiki web. | ||||||||
| Line: 77 to 80 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Read Access Restriction for a Whole TWiki Web | |||||||
| > > | Read Access Restriction by Web | |||||||
| You can define restrictions of who is allowed to view a TWiki web. | ||||||||
| Line: 85 to 88 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Notes for read access restriction: | |||||||
| > > | Read Access Restriction Notes | |||||||
| ||||||||
| Line: 99 to 103 | ||||||||
| ||||||||
| Deleted: | ||||||||
| < < | -- PeterThoeny - 16 Mar 2001 | |||||||
| Changed: | ||||||||
| < < | NOTE: | |||||||
| > > | The SuperAdminGroup | |||||||
The above schema can lock completely a topic in case of a typing error of the ALLOWTOPICCHANGE setting (see UnchangeableTopicBug
| ||||||||
| Line: 110 to 113 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | -- PeterThoeny - 16 Mar 2001 | |||||||
| -- AndreaSterbini - 11 Apr 2001 | ||||||||
| Changed: | ||||||||
| < < | ||||||||
| > > | ||||||||
| Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup, TWikiGroups | ||||||||
Revision 102001-08-29 - MikeMannix
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
TWiki Access ControlTWiki allows you to define restrictions of who is allowed to view a TWiki web, make changes to topics or attach files. | ||||||||
| Line: 99 to 99 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | -- PeterThoeny - 16 Mar 2001 | |||||||
| Changed: | ||||||||
| < < | Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup, TWikiGroups | |||||||
| > > | NOTE: | |||||||
| Changed: | ||||||||
| < < | -- PeterThoeny - 16 Mar 2001 | |||||||
| > > | The above schema can lock completely a topic in case of a typing error of the ALLOWTOPICCHANGE setting (see UnchangeableTopicBug
$superAdminGroup = "TWikiAdminGroup";
Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup, TWikiGroups | |||||||
Revision 92001-08-07 - JohnTalintyre
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
TWiki Access ControlTWiki allows you to define restrictions of who is allowed to view a TWiki web, make changes to topics or attach files. | ||||||||
| Line: 50 to 51 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | Rename Access Restriction for Individual TopicsYou can define restrictions of who is allowed to rename a topic. Note that users need this permission in addition to the CHANGE permission in order to rename a topic. They also need CHANGE access to change references in referring topics. Define one or both of these variables in a topic, preferably at the end of the topic:
* Set DENYTOPICRENAME = Main.SomeBadBoy, Main.SomeBadGirl, Main.SomeHackerGroup
ALLOWTOPICRENAME defines users or groups that are allowed to rename the topic. It is a comma delimited list of users and groups. Example: * Set ALLOWTOPICRENAME = Main.SomeGoodGuy, Main.SomeGoodGirl, Main.TWikiAdminGroup
DENYTOPICRENAME is evaluated before ALLOWTOPICRENAME. Access is denied if the authenticated person is in the DENYTOPICRENAME list, or not in the ALLOWTOPICRENAME list. Access is granted in case DENYTOPICRENAME and ALLOWTOPICRENAME is not defined.
Rename Access Restriction for a Whole TWiki WebYou can define restrictions of who is allowed to do renames for a TWiki web. Define one or both of these variable in the WebPreferences topic:
| |||||||
Read Access Restriction for a Whole TWiki WebYou can define restrictions of who is allowed to view a TWiki web. | ||||||||
Revision 82001-06-08 - PeterThoeny
| Line: 65 to 65 | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| ||||||||
Revision 72001-03-16 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
| Added: | ||||||||
| > > | TWiki Access Control | |||||||
| TWiki allows you to define restrictions of who is allowed to view a TWiki web, make changes to topics or attach files. IMPORTANT NOTE: Think twice before restricting read or write access to a web or a topic, because an open system where everybody can contribute is the essence of the WikiCulture. Experience shows that unrestricted write access works very well because: | ||||||||
| Line: 6 to 8 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Users and Groups | |||||||
| > > | Users and Groups | |||||||
| Access control is based on users and groups. | ||||||||
| Line: 22 to 24 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Write Access Restriction for Individual Topics | |||||||
| > > | Write Access Restriction for Individual Topics | |||||||
| You can define restrictions of who is allowed to make changes to a topic or attach files to it. | ||||||||
| Line: 36 to 38 | ||||||||
| DENYTOPICCHANGE is evaluated before ALLOWTOPICCHANGE. Access is denied if the authenticated person is in the DENYTOPICCHANGE list, or not in the ALLOWTOPICCHANGE list. Access is granted in case DENYTOPICCHANGE and ALLOWTOPICCHANGE is not defined. | ||||||||
| Changed: | ||||||||
| < < | Write Access Restriction for a Whole TWiki Web | |||||||
| > > | Write Access Restriction for a Whole TWiki Web | |||||||
| You can define restrictions of who is allowed to make changes to a TWiki web. This includes creating new topics, changing topics or attaching files. | ||||||||
| Line: 48 to 50 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Read Access Restriction for a Whole TWiki Web | |||||||
| > > | Read Access Restriction for a Whole TWiki Web | |||||||
| You can define restrictions of who is allowed to view a TWiki web. | ||||||||
| Line: 73 to 75 | ||||||||
| Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup, TWikiGroups | ||||||||
| Changed: | ||||||||
| < < | -- PeterThoeny - 20 Jan 2001 | |||||||
| > > | -- PeterThoeny - 16 Mar 2001 | |||||||
Revision 62001-02-26 - PeterThoeny
| Line: 57 to 57 | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
| Added: | ||||||||
| > > |
| |||||||
| ||||||||
Revision 52001-01-21 - PeterThoeny
| Line: 57 to 57 | ||||||||
|---|---|---|---|---|---|---|---|---|
| ||||||||
| Added: | ||||||||
| > > |
| |||||||
| ||||||||
Revision 42001-01-21 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
| Changed: | ||||||||
| < < | TWiki allows to define some restrictions of who is allowed to make changes and attach files to topics. | |||||||
| > > | TWiki allows you to define restrictions of who is allowed to view a TWiki web, make changes to topics or attach files. | |||||||
| Changed: | ||||||||
| < < | IMPORTANT NOTE: Think twice before restricting write access to a web or a topic, because an open system where everybody can contribute is the essence of the WikiCulture. Experience shows that unrestricted write access works very well because: | |||||||
| > > | IMPORTANT NOTE: Think twice before restricting read or write access to a web or a topic, because an open system where everybody can contribute is the essence of the WikiCulture. Experience shows that unrestricted write access works very well because: | |||||||
| ||||||||
| Line: 22 to 22 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Access Control for Individual Topics | |||||||
| > > | Write Access Restriction for Individual Topics | |||||||
| Changed: | ||||||||
| < < | You can define some restrictions of who is allowed to make changes and attach files to a topic. | |||||||
| > > | You can define restrictions of who is allowed to make changes to a topic or attach files to it. | |||||||
Define one or both of these variables in a topic, preferably at the end of the topic:
| ||||||||
| Line: 36 to 36 | ||||||||
| DENYTOPICCHANGE is evaluated before ALLOWTOPICCHANGE. Access is denied if the authenticated person is in the DENYTOPICCHANGE list, or not in the ALLOWTOPICCHANGE list. Access is granted in case DENYTOPICCHANGE and ALLOWTOPICCHANGE is not defined. | ||||||||
| Changed: | ||||||||
| < < | Access Control per TWiki Web | |||||||
| > > | Write Access Restriction for a Whole TWiki Web | |||||||
| Changed: | ||||||||
| < < | You can define some restrictions of who is allowed to make changes and attach files to topics or create new topics in a TWiki web. | |||||||
| > > | You can define restrictions of who is allowed to make changes to a TWiki web. This includes creating new topics, changing topics or attaching files. | |||||||
Define one or both of these variable in the WebPreferences topic:
| ||||||||
| Line: 48 to 48 | ||||||||
| ||||||||
| Added: | ||||||||
| > > | Read Access Restriction for a Whole TWiki Web
You can define restrictions of who is allowed to view a TWiki web.
Define one or both of these variable in the WebPreferences topic:
| |||||||
| Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup, TWikiGroups | ||||||||
| Changed: | ||||||||
| < < | -- PeterThoeny - 28 Oct 2000 | |||||||
| > > | -- PeterThoeny - 20 Jan 2001 | |||||||
Revision 32000-12-14 - PeterThoeny
| Line: 40 to 40 | ||||||||
|---|---|---|---|---|---|---|---|---|
| You can define some restrictions of who is allowed to make changes and attach files to topics or create new topics in a TWiki web. | ||||||||
| Changed: | ||||||||
| < < | Define one or both of these variable in the WebPreferences topic: | |||||||
| > > | Define one or both of these variable in the WebPreferences topic: | |||||||
| ||||||||
| Changed: | ||||||||
| < < |
| |||||||
| > > |
| |||||||
| Changed: | ||||||||
| < < | Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup, TWikiGroups | |||||||
| > > | Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup, TWikiGroups | |||||||
|
-- PeterThoeny - 28 Oct 2000 | ||||||||
Revision 22000-11-08 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
| TWiki allows to define some restrictions of who is allowed to make changes and attach files to topics. | ||||||||
| Changed: | ||||||||
| < < | IMPORTANT NOTE: Is is recommended to use the access control feature only if absolutely necessary because it goes against the free WikiCulture, where everybody is invited to contribute to any topic. | |||||||
| > > | IMPORTANT NOTE: Think twice before restricting write access to a web or a topic, because an open system where everybody can contribute is the essence of the WikiCulture. Experience shows that unrestricted write access works very well because:
| |||||||
| Users and Groups | ||||||||
| Line: 44 to 48 | ||||||||
| ||||||||
| Changed: | ||||||||
| < < | Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup | |||||||
| > > | Related topics: TWikiPreferences, WebPreferences (in every web), TWikiAdminGroup, TWikiGroups | |||||||
|
-- PeterThoeny - 28 Oct 2000 | ||||||||
Revision 12000-10-29 - PeterThoeny
| Line: 1 to 1 | ||||||||
|---|---|---|---|---|---|---|---|---|
| Added: | ||||||||
| > > | TWiki allows to define some restrictions of who is allowed to make changes and attach files to topics.
IMPORTANT NOTE: Is is recommended to use the access control feature only if absolutely necessary because it goes against the free WikiCulture, where everybody is invited to contribute to any topic.
Users and Groups
Access control is based on users and groups.
Users are defined by the user topics in the Main web, i.e. TWikiGuest
* Set DENYTOPICCHANGE = Main.SomeBadBoy, Main.SomeBadGirl, Main.SomeHackerGroup
ALLOWTOPICCHANGE defines users or groups that are allowed to make changes to the topic. It is a comma delimited list of users and groups. Example: * Set ALLOWTOPICCHANGE = Main.SomeGoodGuy, Main.SomeGoodGirl, Main.TWikiAdminGroup
DENYTOPICCHANGE is evaluated before ALLOWTOPICCHANGE. Access is denied if the authenticated person is in the DENYTOPICCHANGE list, or not in the ALLOWTOPICCHANGE list. Access is granted in case DENYTOPICCHANGE and ALLOWTOPICCHANGE is not defined.
Access Control per TWiki Web
You can define some restrictions of who is allowed to make changes and attach files to topics or create new topics in a TWiki web.
Define one or both of these variable in the WebPreferences topic:
| |||||||
View topic | History: r43 < r42 < r41 < r40 | More topic actions...
Ideas, requests, problems regarding TWiki? Send feedback
Note: Please contribute updates to this topic on TWiki.org at TWiki:TWiki.TWikiAccessControl.